The Internet of Things (IoT) describes the increasingly sophisticated, complex network of online, connected devices that enhance our cars, homes, and cities. According to IoT Analytics, the global number of connected IoT devices is expected to grow at a CAGR (compound annual growth rate) of 22% and reach 27 billion IoT connections by 2025.
From smart homes and cities, driverless cars, and pollution control to the transference of data to monitor important processes and provide new insights, boost efficiency, and allow companies to make more informed decisions – the fast growth of IoT is changing the way we live and work.
With the dramatic rise in connected devices also comes an increased need for security. Addressing cybersecurity risk can help companies leverage IoT opportunities while tackling the vulnerabilities that are part of the latest regulatory guidance. Regulatory bodies and government organizations worldwide are realizing the dangers and risks of connected devices that are not built with proper security in mind — and responding with a variety of regulations for which companies will be forced to comply.
Complex or innovative projects, such as IoT, have specific security requirements that traditional security tools do not always provide. The development environment and the variety of device types add even more complexity to protecting IoT against threats.
Report findings
Below are the findings of the Kaspersky Global Corporate IT Security Risks Survey (ITSRS) which is a global survey of IT workers. A total of 4,303 interviews from businesses with more than 50 employees were conducted across 31 countries in May-June 2021.
Throughout the report, businesses are referred to as either SMBs, (small and medium-sized businesses with 50 to 999 employees), or enterprises, (businesses with over 1,000 employees). Not all survey results are included in this report.
The report also includes opinion pieces by experts: Eric Kao, Director, WISE-Edge+ of Advantech, and Stephen Mellor, Chief Technology Officer at the Industry IoT Consortium (IIC).
In 2021, 53% of organizations abandoned new business projects due to an inability to address cybersecurity risks, and 74% faced a situation where there was a lack of an appropriate security solution. 64% of businesses already maintain or use IoT solutions. However, the risk of a cybersecurity breach is the biggest concern for 57% of organizations that are planning to implement IoT. 52% of organizations are worried about collecting big data from IoT devices because of the risk of cyber sabotage and espionage. 43% of businesses surveyed indicated that at least one type of IoT was not protected, highlighting a clear need for dedicated cybersecurity tools.
Specific cybersecurity demands
When it comes to cybersecurity risk, no two organizations or innovations are the same.
According to Siemens, cybersecurity is a rapidly changing battlefield that requires awareness, continuous vigilance, and a consolidated response from everyone involved. Cyber protection is not a product that you simply invest in once and then forget about. It is an ongoing process.
Implementing the same cyber-risk controls everywhere and equally doesn’t always work. Applying sectional protections that leave some vital information assets vulnerable while focusing too closely on less critical ones is also not a way out for enterprises adopting innovations such as IoT. Cybersecurity budgets, meanwhile, compete for limited funds with technology investments intended to make the organization more competitive.
However, sometimes the issue is meeting very specialized cybersecurity requirements, which is not easy to do. In 2021, 74% of companies faced at least one situation where there was a lack of appropriate security solutions, and 53% abandoned implementing new IT solutions, updating corporate policy, or even launching a new business project because they were unable to address cybersecurity risks.
Looking broader, every second organization (53%) had to figure out troubles with their cybersecurity solutions. Research found performance (35%) and maintenance (34%) issues were the most common ones. However, these should be expected just as with any other IT and technology. These routine tasks are followed by compatibility issues (34%) with specialized software or firmware, such as industrial and manufacturing. That said, IT security teams have to find compromises and workarounds.
The timely patching and software updates is of great importance. However, this can present a significant problem too, with 28% of businesses reporting vulnerabilities that are impossible to patch for the following reasons (see Figure 1):

Figure 1: Problems with patching
The range of obstacles and challenges facing organizations implementing cyber-protection for IoT are exacerbated by the diverse set of industries in which they operate.
Reward vs. risk: Leveraging IoT solutions globally
IoT is widespread across a range of diverse business industries – from retail and transportation infrastructure to energy, industrial and smart cities.
Overall, 64% of businesses maintain or use an IoT solution (see Figure 2).
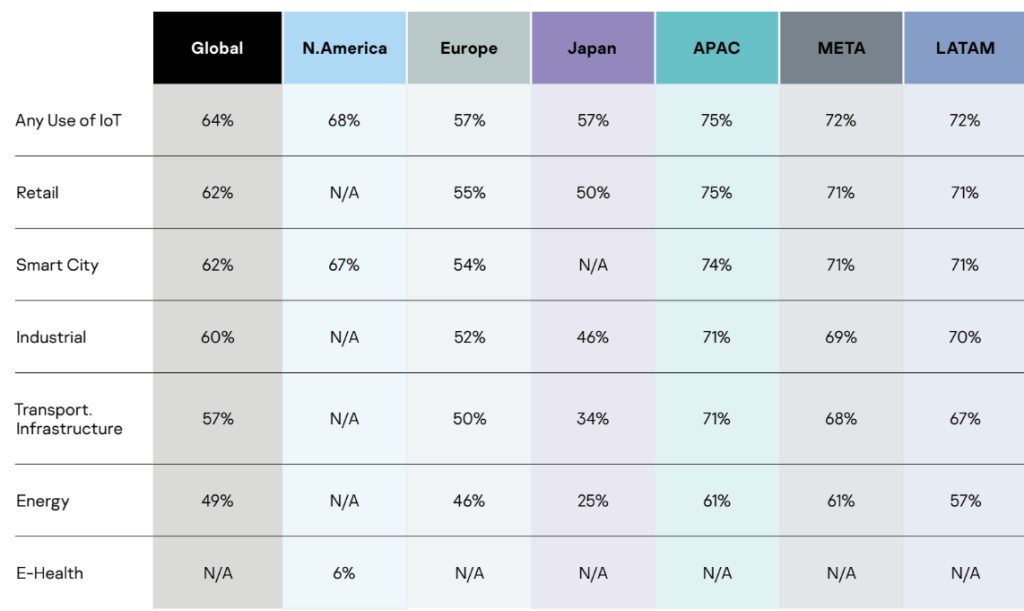
Figure 2: Global industry accelerates widespread IoT adoption
The type of devices also includes a vast array, such as security and alarm sensors, video surveillance, machine conditioning monitoring, EV charging stations, and energy distribution automation (see Figure 3).
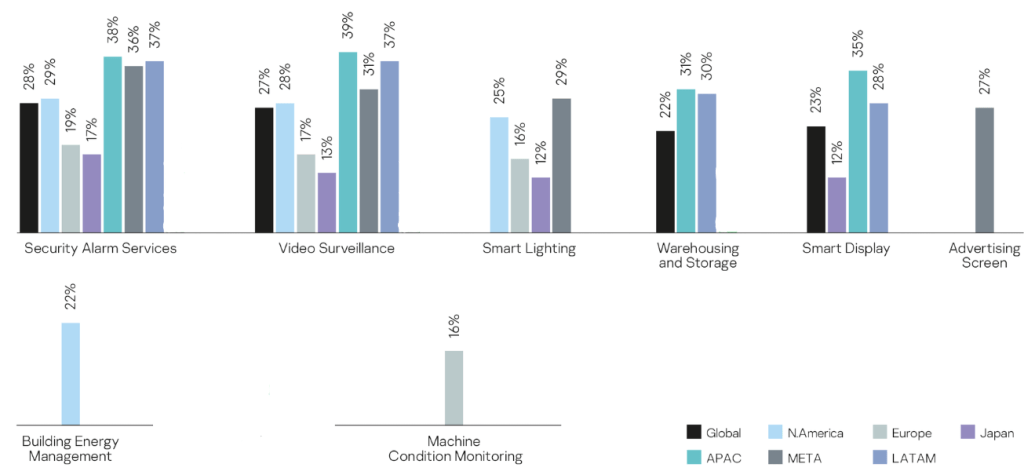
Figure 3: Percentage of companies planning to increase the use of above IoT solutions
IoT devices are used in a wide range of businesses and industries and are ideal for making the most of data analysis. These devices contain chips, cameras, sensors and many other components that receive and collect huge amounts of valuable data. Analysis of this data helps to improve the efficiency of equipment, predict anomalies or damage, and find the most optimal way of organizing manufacturing process
The IoT introduces a wide range of new security risks and challenges to devices, platforms and operating systems, their communications and even the systems to which they’re connected (such as using IoT devices as an attack entry point).
Unfortunately, many IoT devices have little or no protection at the software and infrastructure levels. They are often unsupported and have no updates from the vendor. Implementing IoT solutions on top of existing legacy systems, which were once standalone and unconnected, will also create vulnerable targets for cyberattacks.
Indeed, despite the growing rise of IoT, more than half of the organizations surveyed are concerned about cybersecurity breaches and data compromises when implementing IoT (57%). A lack of resources or budget constraints is cited as the second reason by a wide margin (35%) (see Figure 4).

Figure 4: Biggest Barriers to IoT implementation
When it comes to gaining value from the information collected by the device, 63% of organizations use big data or telemetry from IoT devices for business purposes. When asked about their specific concerns for collecting big data from IoT devices, organizations are particularly worried about the risks of cyber-sabotage, espionage and other advanced threats (52%). Companies are also concerned about the physical protection of their IoT devices (40%), connections on the cloud (38%) and lack of in-house expertise (34%) (see Figure 5).
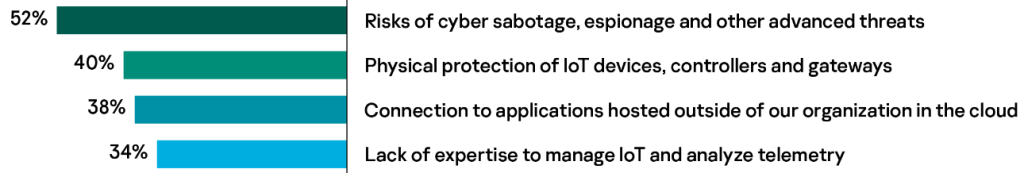
Figure 5: Key concerns for big data in IoT
42% of organizations reported being impacted by cybersecurity incidents affecting IoT cloud services (public clouds infrastructure), while 41% cited incidents affecting IoT gateway and network devices (see figure 6).
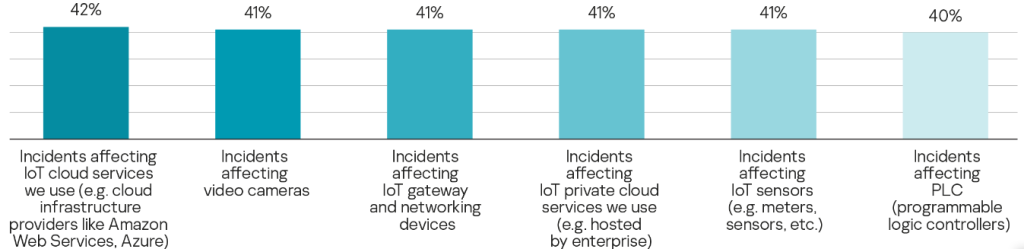
Figure 6: Prevalence of attacks on IoT across business areas
Protecting IoT and systems with the highest cybersecurity demands
The good news is that research found 43% of businesses have some form of IoT cybersecurity measures in place. However, an equal number (43%) of the businesses reported having at least one type of IoT that was not protected.
Organizations face several challenges when protecting IoT. The sheer scale and variety of devices, operating systems, software, and hardware components make it difficult to secure IoT platforms from potential data breaches and attacks on the whole network.
Unlike hardware and software for PCs or mobiles which are well researched and standardized, it is impossible to study all IoT devices and ensure the reliability of conditions for their development, making errors, vulnerabilities and undeclared functions inevitable.
Another setback is that there are many open-source software platforms for IoT development. These components are often not tested for cybersecurity, so vulnerabilities can find their way into the developed product and persist for many versions. One example of this would be a ‘zero-day’ attack, which takes place when hackers or malicious actors exploit the flaw before developers have a chance to address it. These types of attacks are especially dangerous because once criminals have infiltrated a network, they can either attack immediately or sit and wait for the most advantageous time to do so.
In 2021, experts at Israeli company JSOF discovered 19 zero-day vulnerabilities, some critical, affecting hundreds of millions of IoT devices. These vulnerabilities – named Ripple20 – were found in the TCP/IP library of Treck Inc., which JSOF has been developing for more than two decades. The library is present in a wide range of IoT solutions, affecting items from home and office printers to industrial and medical equipment.
But using a standard endpoint anti-malware protection solution is not the way out of this problem. Moreover, there are some devices on which anti-malware solutions cannot be installed due to insufficient performance or resources.
A further challenge for businesses is the difficulty of rolling out updates to IoT devices and platforms. Unlike the more versatile PCs and mobile devices, for which IT departments usually have effective tools for timely updates, IoT solutions can consist of many different applications, systems, and pieces of software with no single approach to updating and patching. Updating such systems is a laborious and not always feasible task.
Responses to IoT security challenges
In order to respond to IoT security challenges and provide help to companies requiring specific cybersecurity protection, activities on different levels must emerge.
There is a movement towards standardizing the development and implementation of IoT platforms to make them more reliable and secure. Such initiatives are born in associations like The Institute of Electrical and Electronics Engineers (IEEE), The International Telecommunication Union (ITU), The European Telecommunications Standards Institute (ETSI), and so on. National-level policies that require specific cybersecurity measures from local players have already begun being implemented.
There are also recommendations for businesses on how to approach building secure IoT systems or how to assess the state of IoT solutions already in place, such as one from the Industry IoT Consortium – “IoT Security Maturity Model“. It guides organizations through processes that will help them adopt sufficient security measures for specific cases.
Common recommendations for IoT security involve using encryption and strict password policies, vulnerability management, network segmentation, and Zero Trust model, as well as firewalls and dedicated protection for cloud infrastructures with which IoT devices connect. These practices are essential for all critical operational technology systems.
Additionally, there is a specific approach to IoT security, called Cyber Immunity, that is necessary when protection is an innate function of the IoT platform. Cyber Immunity is focused, not on reducing the number of potential vulnerabilities, but on creating conditions where the exploitation of vulnerabilities does not affect the basic functions of the overall system. Therefore, even if an application is compromised, it will not affect the operation of the entire platform.
This can be achieved with specific operating system and methodology for platform development. This operating system uses a microkernel architecture, with only a few thousand lines of code, which minimizes the risk of vulnerabilities and reduces the attack surface. This structure, using a minimal number of trusted components in the OS, along with security domain isolation, scanning of interprocess communications, and MILS architecture (Multiple Independent Levels of Security), ensures that most types of attacks are unable to affect the system’s functions.





