The IoTAC project aims to deliver a secure and privacy-friendly IoT architecture that will facilitate the development of more resilient IoT service environments. Our system, comprising of a secure gateway, runtime security applications and cloud-based service platforms, will provide comprehensive protection for service environments of various IoT domains. The technology will not only protect new deployments but can also enhance the security level of legacy operations.


Concept
IoTAC has a multi-layer approach to improve IoT security. We elaborate a security framework, call it Security baseline which covers all aspects of system development from requirement specification, through design, development and testing, to certification with associated KPIs and validation measures.
The Security Baseline is defined based on best practices, on well-established industrial standards and the research results of the project.
In the IoTAC architecture we deploy a combination of state of the art technologies (in some cases we provide the state of the art through patented or patent pending solutions) and extend them with new inherently secure processes and workflows. Security countermeasures are implemented both at hardware- and at software-level, which treat privacy and data security as topmost priorities.
The IoTAC technology encompasses multiple security layers
(i) advanced access control mechanism based on new interactions and workflow using chip cards or other types of secure elements and PKI technology;
(ii) runtime protection of the architecture, comprising a secure gateway, a runtime data collection and monitoring system, honeypots, AI and ML algorithms and checkpointing
IoTAC will also implement Security-by-Design based methodology and supporting platform for integrating security into every step of Software Development Life Cycle as well as for the assessment of software applications running on the IoT architecture.
These will be part of a comprehensive certification program covering software development, architecture design and protection targets. The certification will be based on internationally recognized security standards, best practices and the research results of the project. Certification will be made available through the IoTAC Association to developers and service providers.
IoTAC will also develop SDKs and publish APIs to facilitate the smooth and rapid integration of the IoTAC modules into diverse IoT architectures.
Architecture
IoTAC has selected ISO/IEC CD 30141 IoT Reference Architecture as a starting point for its work. The ISO/IEC 30141 IoT Reference Architecture consists of six main domains, decomposed in a number of intra-domain functional components. However, the functional components are not mandatory, and the final subset of functions for particular IoT implementations depends on the specific IoT application case.
The purpose of the IoTAC framework is to facilitate the production of more secure IoT systems. Our approach focuses on adding security both at IoT architecture level and at the level of software applications that run on its various components. As far as the security of the IoT platform is concerned, this is achieved through the extension of the IoT Reference Architecture by integrating a set of innovative security features, covering all phases of the product/service life-cycle, from design, through development and certification, to operation.
The IoTAC Reference Architecture integrates the security function as a key part of system design. Specifically, security, safety, resilience, trust and privacy are treated as cross-domain functions.
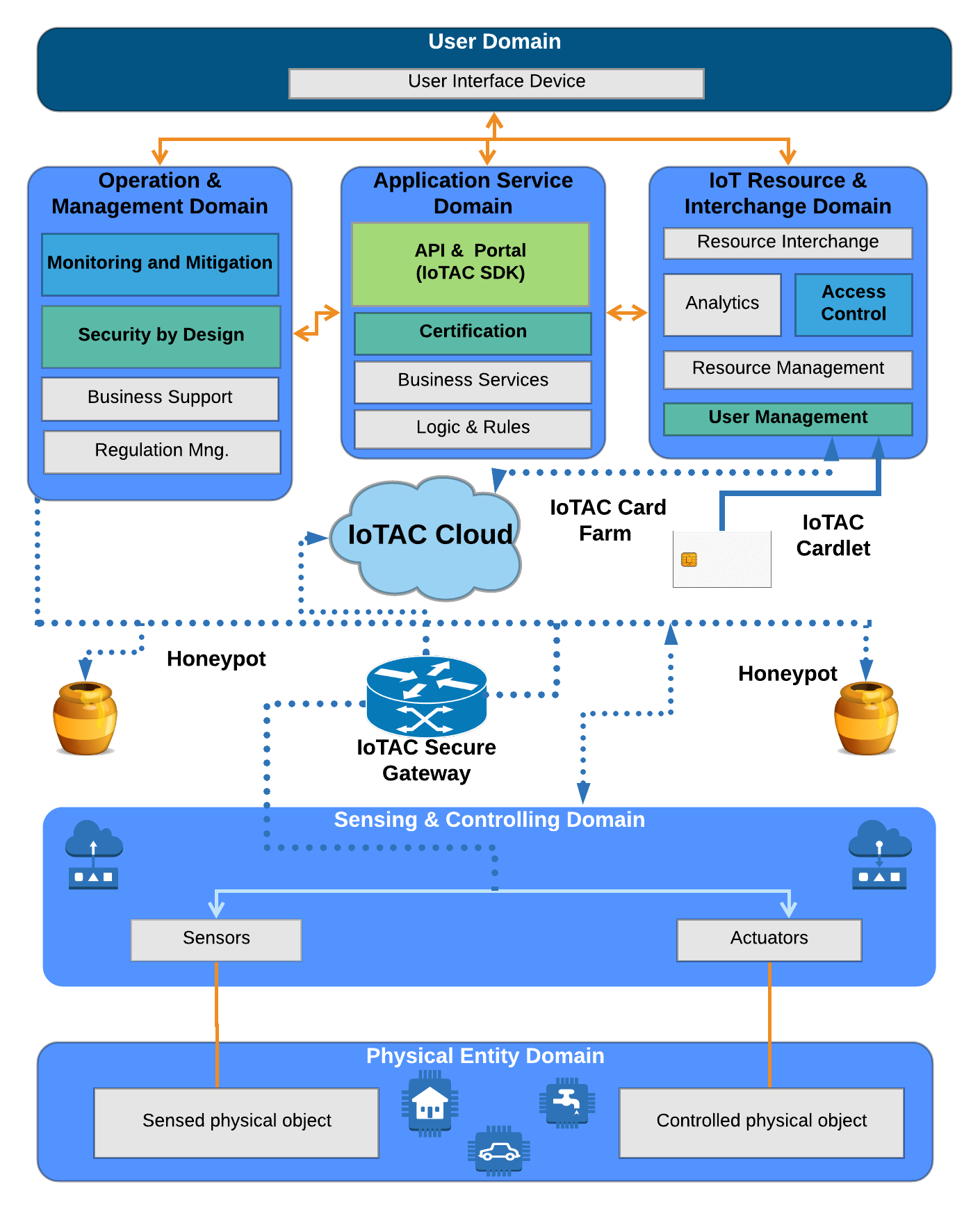
The figure illustrates how IoTAC positions the proposed solution and its structural elements against ISO/IEC 30141 IoT Reference Architecture.
The standard-based functional components which are going to be implemented as a part of IoTAC platform are marked light green in the figure. Components which are marked green, represent newly introduced ones, in order to support novel concepts and mechanisms. Existing components which however, will be modified, or enhanced are shown with blue outlines.
There are two parallel tracks of development. The first track is responsible for the development of all these features that are meant to extend the selected reference architecture of IoT platforms (e.g., cardlets, honeypots, security gateway, monitoring and control layer, etc.). The second branch focuses on the design and development of the IoTAC Software Security by Design (SSD) and the Security Assurance Model (SAM) platforms, which are enabling the development of more secure IoT software applications. The two tracks will meet in the assessment and certification procedure of the security level of the IoT platforms and software applications running on these platforms. In addition IoTAC will develop SDKs and APIs to support users to build more secure IoT services with the least effort relying on the IoTAC architecture.
Modules
SSD platform

enables the development of more secure IoT software applications by treating security at each phase of the overall Security by Design Life Cycle. More specifically, SSD will allow developers of an IoT software application to (i) ensure the correct definition of the security requirements, (ii) ensure the adherence of the produced IoT software application to the originally defined requirements, (iii) evaluate the security level of the IoT software application, and (iv) provide recommendations for security improvement. Hence, SSD is expected to enable the continuous monitoring of the security level of software applications running on IoT platforms throughout their overall development cycle, and the enhancement of their security level through the recommendations that it will provide. Moreover, through innovative requirements engineering SSD is expected to improve efficiency by reducing the time that is required between the conceptualization of the security and privacy aspects and software prototyping in an iterative agile-like fashion.
IoTAC Security Assessment Model

(SAM) platform will provide a formal Certification procedure exposed as a service. The Certification service will perform evaluation of submitted devices and systems and issue certificates about their compliance with the IoTAC framework’s IoT security specifications (Security Baseline). First, a comprehensive checklist of the attributes and security features that an IoT Platform should exhibit in order to be compliant with the IoTAC reference architecture will be compiled. Next, all the running software should exhibit high security level. In other words, all the applications running on the IoT platform should be evaluated first by the SSD platform for their security level. Finally, specific thresholds will be defined for the outputs of the runtime security monitors (e.g., percentage of successful attacks that can be considered tolerable, percentage of the simulated attacks that are blocked by the system, etc.). These thresholds will be defined by KPIs in the security specifications and domain specific SLAs.
Front-end Access Management

comprises of user authentication and authorisation which introduces a novel approach using a secure element (chip cards, TEE, secure token), user cardlet and PKI. The solution detaches transaction management from credential control thus supports a truly decentralized operation. The fact that user credentials are stored in the user’s secure element brings inherent privacy and security as there are no online repositories with sensitive personal information. The authentication and authorisation functions are delegated to the front-end which results in a very simple architecture at the end-points, allowing the highest level security even for the simplest devices. One of the most important features of the proposed architecture and operational procedure is the capability to issue and manage the user credentials on the user’s secure element over-the-air. The architecture supports real time issuance and management (modification and revocation) of the credentials.
IoT-enabled honeypots

will be introduced with the purpose to attract the attention of potential attacker to specific environments that are not part of the actual system. This is expected to reduce the number of attacks to the actual system. It will also enable the monitoring of the attackers in order to better understand their behaviour, allowing the timely adoption of appropriate security countermeasures.
The honeypots will comprise of two layers, one visible to the attackers, and another one that will be dedicated for analysing the attackers’ behaviour. A critical element of the IoTAC IoT-enabled honeypots will be the novel anomaly detection algorithms. Both lightweight and advanced anomaly detection techniques will be developed supporting the early detection of behavioural changes of IoT devices, as well as the identification of potential intrusions and the conduction of root cause analysis for attack patterns
Kaspersky’s Security Gateway

will be enriched with Attack detection and prevention (ADP) and checkpointing features which will be developed through the project. ADP mechanisms will be developed, based on Deep Learning. Emphasis will be given to the adoption of advanced algorithms, and particularly on the Deep Dense Random Neural Networks , in order to achieve better predictive performance with lower demand on computational resources. Checkpointing will be used to introduce new security countermeasures. It is a technique that when an attack is detected, the defender can interrupt the system’s activities surreptitiously in a random manner that cannot be understood by the attacker, and then restart the protected system after some random delay from a safe operating point that was established at the most recent checkpoint.
Runtime Monitoring System (RMS)

will collect security-related data real-time from monitored IoT system components or applications and will store them for further processing. The collected data will be used to drive analytics algorithms that detect patterns of abnormal behaviour. The system will feature lightweight monitoring probs that will be responsible for the data collection and publishing to the monitoring platform. The RMS will provide appropriate configuration and management mechanism over the monitoring probes as well as appropriate data models and data transformation engines that will enable the discoverability and reusability of the collected data. The probe management will be facilitated by an internal probe registry that will maintain the probe information along with their status and will enable the probe creation, reconfiguration and discovery.
AI-based attack detection

A novel technique using the Auto-Associative Random Neural Network (AARNN) is developed and tested to provide highly accurate attack detection of major Botnet attacks. The additional value of this technique lies in its training protocol which relies on normal traffic patterns, without requiring data regarding all the possible attack patterns that the network may encounter. The approach has also been compared on the same data set with two other known Machine Learning methods (Lasso and KNN) and shown to have higher accuracy, and much lower computation times than KNN and slightly higher (but comparable) computation times with respect to Lasso.
Botnet attacks have proved to be one of the major dangers faced by the IoT. Indeed, such insidious attacks do not only take down specific nodes and links between IoT devices and servers that process the data, but they also induce the compromised nodes.





