
- What is a Honeypot?
Honeypots are software designed to detect novel and emerging attack patterns against a specific system. Hence, a vulnerable version of the protected system will be created, which typically represents the easiest way to attack a system. With special preparation, a honeypot serves as a trap that first of all attracts the interest of the attacker and secondly allows the creator to study and find the occurring attacks against the system. Generally, a Honeypot is deployed as a part of the network, although it needs to be properly isolated and protected, but should still contain spoofed information and functionalities that are valuable for the attacker.
To break this down, Honeypots are often classified into three levels of interaction: Low Interaction, Medium Interaction, and High Interaction. These levels of interaction tell us how much the attacker will be able to interact with the system after a successful attack has been executed. As more data is required by an analyst, more interaction needs to be offered; but a higher level of interaction also yields more risks for the network itself.
- Most common attacks against IoT Devices
One of the most important things to consider when creating a honeypot is the concrete attack surface that needs to be tailored to the use case. In the context of the IoTAC project, we have studied the broad spectrum of vulnerabilities and malware attacks that most typically occur on IoT devices. Due to this research, we found Portscans, Login Hacking, Denial of Service, and Malware Infections through vulnerable software to be the most important ones.
- Portscans: Portscans are used to identify vulnerable services on a device. Often just a few ports are probed, but therefore a large network can be scanned very quickly.
- Login Hacking: Weak or public login credentials can be used to enter a service of the device or credentials can be bruteforced.
- Denial of Service / Denial of Sleep: A network service can be flooded by requests that allocate resources to keep the device busy or deplete its battery. A device can also be tricked to participate in a flood to attack other devices without knowing what it is doing.
- Malware Infections through vulnerable software
Software vulnerabilities can create unknown entry points into a system that cannot be mitigated by any countermeasure.
All in all, most attacks follow the goal to make the IoT device a bot that can be used for larger attacks in the future. This is because IoT devices have low computational resources, their assets are often of low value and their administrative power is very limited. However, by controlling hundreds and millions of these small (powerless) network devices, attacks can bundle and leverage heavy attacks even against the biggest services and make them unavailable.
- Building Honeypots for the IoTAC architecture
In the context of the IoTAC project, we are aiming to make use of this proactive idea to counter upcoming attacks against the network of IoT devices. Hence a virtualized honeypot solution will be a fundamental part of the overall IoTAC design.
Thereby we will make use of a two-world approach. First, we will integrate classical detection techniques to detect the most common attacks, such as Portscans, Login Hacking, DoS, and malware infections. Second, an advanced detection logic, based on a distributed learning approach will enable a new level of security. With a sufficient number of collaborating network nodes, we will be able to detect Portscan, Bruteforce, and DoS attempts even before they finish, just by exchanging current threat information between the nodes and using network intelligence.
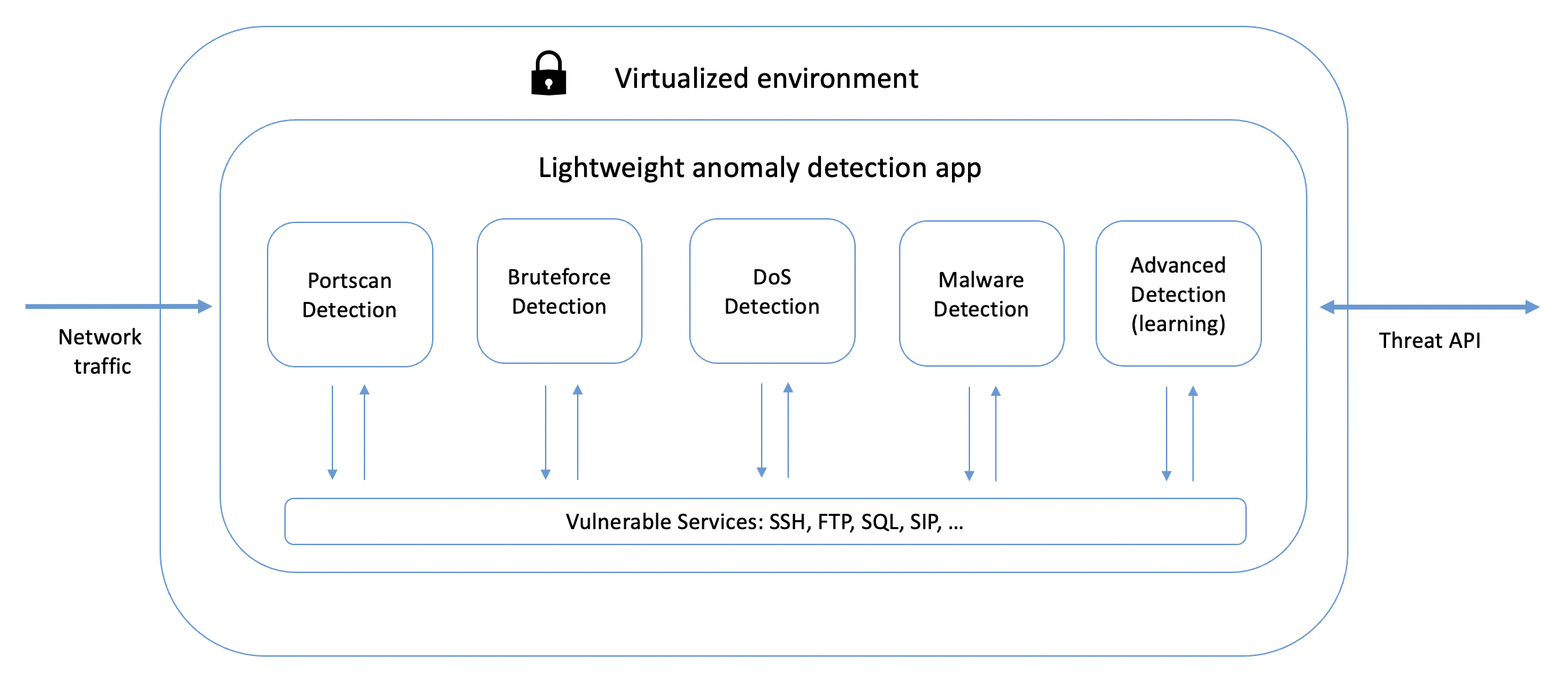
Virtualized Honeypot design with active detection modules for each of the most common attacks against IoT devices.
Based on these principles the IoTAC architecture will integrate virtualized high-performance honeypots that will feature various anomaly detection solutions, as part of its detection engine. Each of these algorithms will be lightweight to fit the use-case of IoT applications and can be tailored by the user to its actual application. This sophisticated detection engine will operate in real-time in a virtualized environment, to learn from occurring attacks and proactively protect the network against upcoming attacks.





