Certification ensures that a process or product meets the requirements of a known standard or specification, often audited by an independent third party. Validation ensures that a product meets pre-determined requirement specifications and can be seen as “sub-process” of certification. In both cases, those standards or specifications are usually the basis for validation and certification and thus, are on national or international level recognized. In case of security certification, the Common Criteria, standardized under ISO/IEC 15408 is a widely known example where the developer of a product implements the requirements on process and product level, an independent evaluation facility performs additional security evaluation, and an independent third-party audits the whole process and finally issues a certificate.
The rules for applying an evaluation process that eventually leads to the issuance of a certificate are defined within a certification scheme. Currently, there are several national and European activities towards a certification scheme for IoT products, e.g. EN 303 645 that has been released by the European Telecommunication Standardization Institute (ETSI) provides minimal security requirements for consumer IoT devices, and the German Federal Office for Information Security BSI published a technical guideline a few ago that specifies minimal security requirements for broadband routers (BSI TR-03148). A list of more national certification schemes in the domain of IoT is listed in [IOT_SCHEMES]. Because of this heterogeneity and parallelism, certified products or processes are only acknowledged in a very small scope. There is an uneven comparison because of the absence of a common cybersecurity certification framework that poses market barriers for new companies and reduces trust. Payment cards, such as credit cards, would not be successful without a security certification such as PCI-DSS that would build trust of the market players.
This gap, a missing European cybersecurity certification, motivated the European Commission to adopt a policy, the Regulation (EU) 2019/881, Cybersecurity Act (CSA) [CSA], that Europe should develop meaningful standards and avoid conflicting-competing initiatives. The European Union Agency for Cybersecurity ENISA [ENISA] supports the European Commission with this intention. The Cybersecurity Act, , forms the basis for those activities and bolster the ENISA with a significant increase in its financial and human resources. Stakeholders from the industry, the national authorities as well as standardization bodies are supporting the ENISA in its activities.
To achieve the goal of a homogeneous European Cybersecurity Certification Scheme (ECCS) landscape, the ENISA provide a well-defined process to develop ECCSs as shown in Figure I.
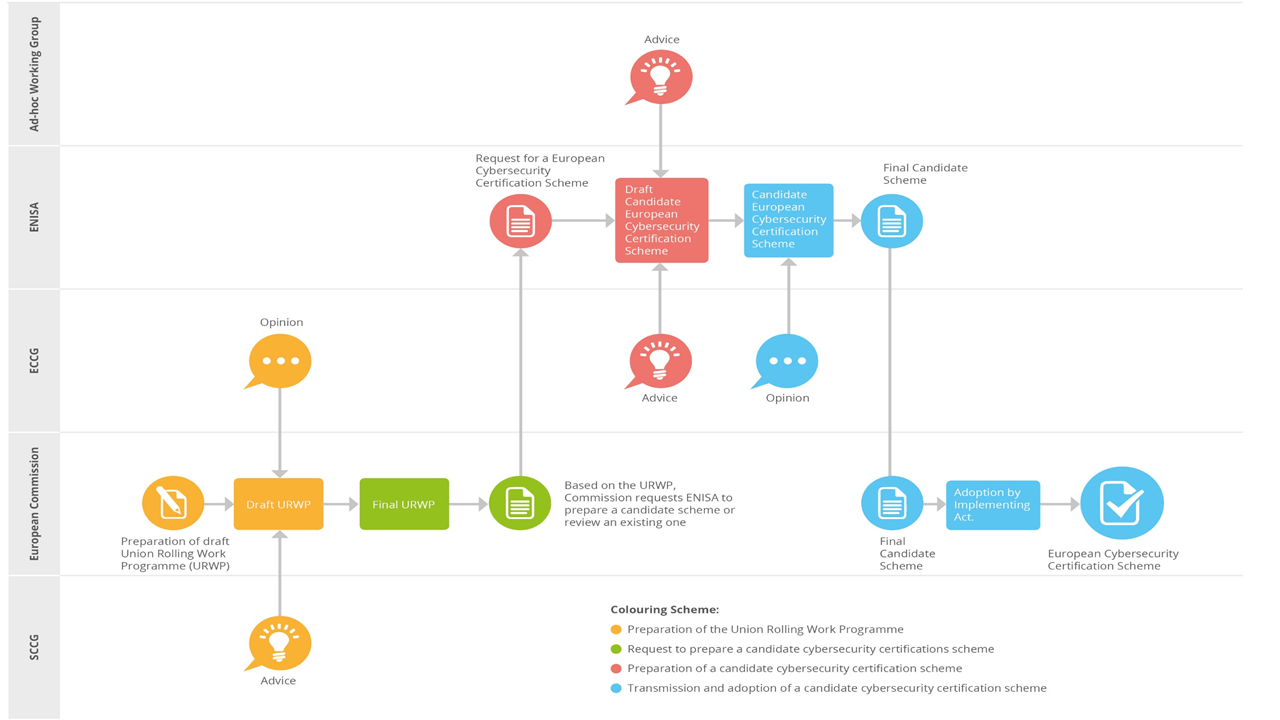
Figure I ENISA Certification Scheme Process
Next to ENISA, the process is mainly driven by the European Commission and two expert groups, i.e. the Stakeholder Cybersecurity Certification Group (SCCG) [SCCG] and the European Cybersecurity Certification Group (ECCG) [ECCG]. The former is a group of up to 50 members from organizations in the broad sense of the word, including academic institutions, consumer organizations, conformity assessment bodies, standard developing organizations, companies and trade associations. The ECCG is a group of representatives of national cybersecurity certification authorities or representatives of other relevant national authorities. Both groups represent the European community in the sense of this context.
The first stage of the European standardization process is a Union Rolling Work Programme (URWP) that is based on advice of the SCCG in case of the topic, scope or domain of a future candidate scheme. The ENISA is requested by the European Commission to prepare a candidate scheme or review an existing one based on the URWP. During the stage of creating the Final Candidate Scheme, the ECCG and the Ad-hoc Working Group support ENISA in this process. The latter is a group of non-permanent stakeholders, in contrast to the SCCG and ECCG, that can advise the Draft Candidate ECCS (e.g. scoping, pre-qualification of elements to be included and reviewing). The membership to an ad-hoc working group is intended to achieve broad representation in the interest groups and based on the modalities of the CSA[1] [AWG]. In addition, ENISA can also request public consultation for candidate schemes (generally for reviewing). The last stage is the Adoption of the Final Candidate Scheme by the implementing act that results in an ECCS.
Currently, there are two certification schemes actively developed. The ICT product Cybersecurity Certification scheme based on SOG-IS and Common Criteria (EUCC) and the Cybersecurity Certification Scheme on Cloud Services (EUCS). Both are already well advanced, and the start of the implementing act is expected in spring 2021. The timeline can be seen in Figure II.
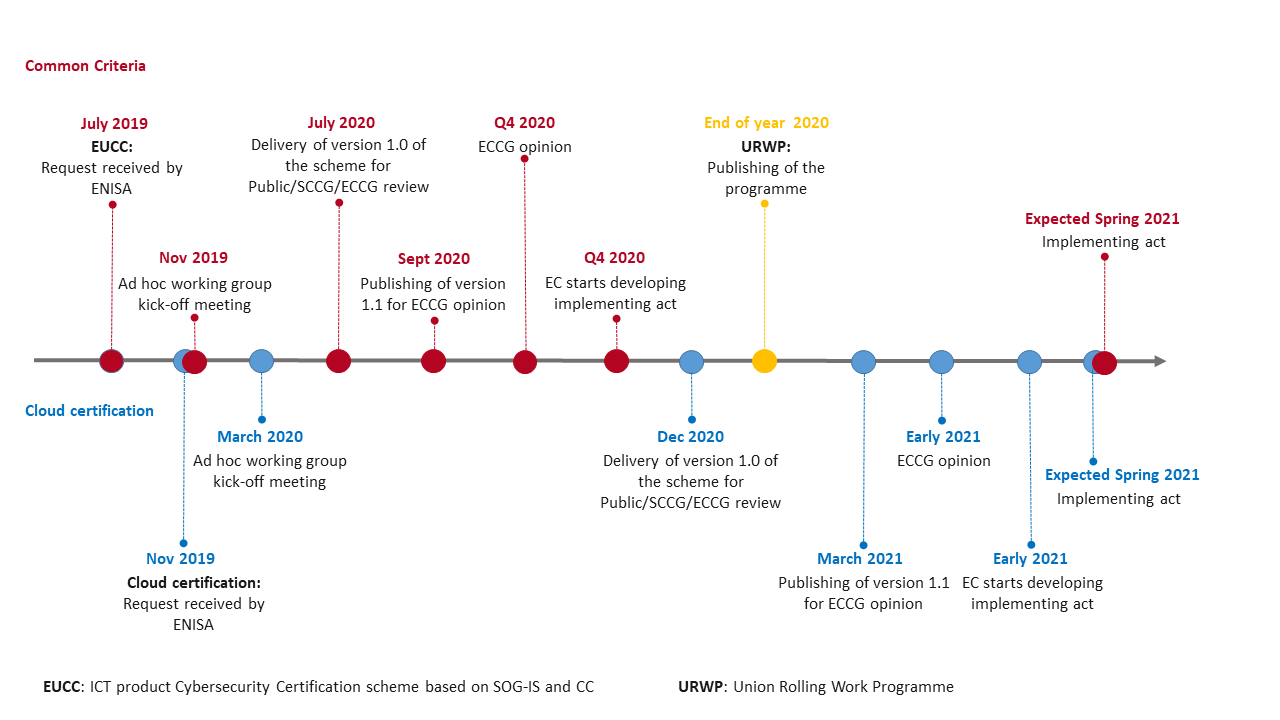 Figure II Timeline for the Certification Scheme EUCC and EUCS
Figure II Timeline for the Certification Scheme EUCC and EUCS
In addition, a future candidate scheme might be IoT, based on the results of the EU survey on the URWP for European cybersecurity certification [CR_URWP]. The majority of the SCCG respondents endorse a candidate IoT scheme. As with the EUCS, the candidate IoT scheme will be defined with cybersecurity best practices across three levels of assurance: basic, substantial and high. The main views regarding cybersecurity are the different lifecycles of IoT products, the connectivity of products, the demand of security by design, the coherence with legal (EU and national) obligations and the handling of product legacies.
Other topics for future candidate schemes are for example Industrial Automation Control Systems (IACS) and 5G.
During the IoTAC project, approaches will be pursued to make sure that the proposed architecture and developed platform are widely accepted. Firstly, there will be a scheme with conformance requirements to validate the technical results of the project. On the other hand, the development of its own cybersecurity certification scheme won’t be a part of the project’s results. According to the directions defined in CSA, IoTAC will rather align with European activities, in particular with the ENISA activities presented above.
Currently, it is planned to adopt the EUCC and EUCS when they are done, since the topic and the expected due date are fitting perfectly into the IoTAC project scope. Furthermore, the IoTAC consortium will actively contribute to and participate in creating future candidate certification schemes, like the most probable candidate IoT scheme. With the knowledge and insights coming from the project and its partners, the IoTAC project can give valuable feedback to such a scheme with regards to cybersecurity.
[1] Article 20(4) of Regulation (EU) 2019/881
[ENISA] ENISA certification landing page https://www.enisa.europa.eu/topics/standards
[CSA] Regulation (EU) 2019/881 (Cybersecurity Act) https://eur-lex.europa.eu/eli/reg/2019/881/oj
[AWG] Ad-hoc Working Group calls https://www.enisa.europa.eu/topics/standards/adhoc_wg_calls/
[IOT_SCHEMES] A Cartography of Security Certification Schemes/Standards for IOT https://www.eurosmart.com/wp-content/uploads/2020/02/2020-01-27-Eurosmart_IoT_Study_Report-v1.2.pdf
[SCCG] https://ec.europa.eu/digital-single-market/en/stakeholder-cybersecurity-certification-group
[ECCG] https://ec.europa.eu/digital-single-market/en/european-cybersecurity-certification-group
[CR_URWP] Consultation Report on Draft Union Rolling Work Programme https://ec.europa.eu/newsroom/dae/document.cfm?doc_id=73318





