As part of the IoTAC project, the IoT-enabled Honeypot solution will be deployed in four pilot cases: a smart home setup, a prosumer cell operation, a connected car network, and a drone operation use case. In each case, the honeypot will play a pivotal role in detecting and recording malicious activity threatening the IoT application field devices. Today, we will discuss how we integrate the IoT Honeypot and how an IoT application developer can achieve this with the IoTAC framework.
# Configure the Honeypots
To initiate a Honeypot, the application developer must configure it using a centralized configuration on the honeypot hosting device. We provide an initial set of configurations that can be remixed according to the specific use case to make it as simple as possible. The configuration allows us to enable various interfaces and services such as SSH, FTP, or MySQL. At best, the developer will enable a similar set of services that perfectly mimic the IoT field devices to be protected. The most basic services are interactive and monitored by our detection modules to spot any form of brute-force login hacking, port scanning, DoS attacks, or malware activity. More application-specific services can be prepared to echo a set of predefined responses and get some threat information without modeling the entire system. To enable the advanced detection capabilities, at least two honeypot instances need to be initiated. These can be identical configurations of the honeypot, but they also can mimic different devices in a more diverse set of IoT field devices. These honeypots will share their knowledge with other honeypots to identify attack patterns across the whole IoT field device network.
# Connect the Honeypots
Like the IoT field devices, the honeypots are very loosely coupled with other components. This makes integration very easy. We just provide the communication details to reach the IoTAC Application Server, which will fetch and store the threat information in its observation repo. Here we log every relevant interaction and report the key details of any occurring attack pattern happening. If more information is needed, a manual analysis is required where more data can be accessed and secured on the honeypot itself.
# Monitor the Honeypots
This functionality is closely related to the IoTAC dashboard. Hence, the last step of integrating the IoTAC honeypot means creating meaningful filters and alerts to analyze the aggregated data stream. These filters can include different thresholds for attack notifications or list the responsible contacts that need to be informed on a certain level of severity. Since this is very application-specific, we only provide a few basic examples to provide a quick and easy start.
To make this process as flawless as possible, the IoTAC framework will provide a set of examples and use cases that can be reused and modified by an IoT application developer.
One of these examples, covering a smart home environment we are currently working on, can be seen in Figure 1.
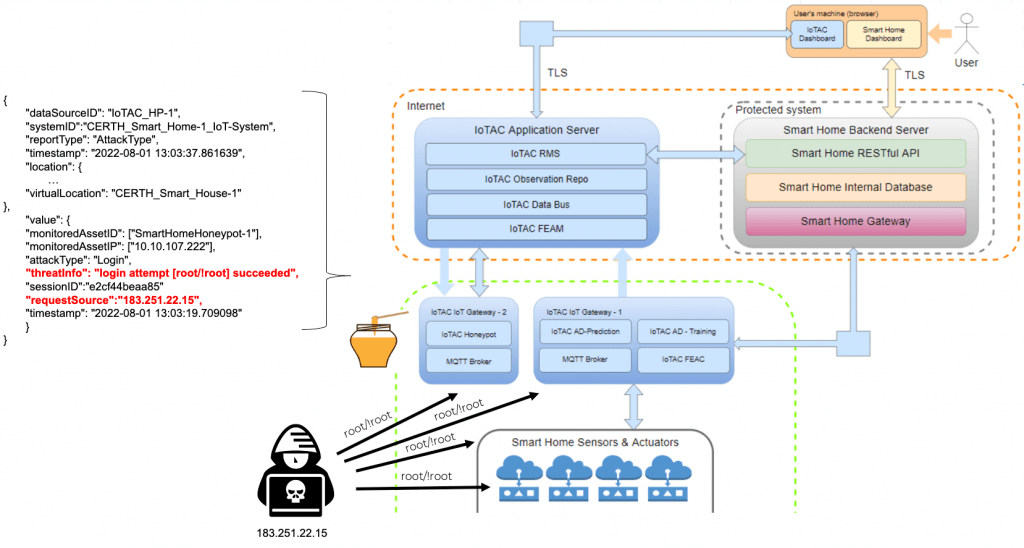
Figure 1: A honeypot for a smart home environment
In summary, there are three quick steps to integrate IoTAC honeypots into an IoT application.
1. Customize the honeypot interfaces through the configuration to look like a field device
2. Establish the network connectivity to the IoTAC Application Server
3. Configure the dashboard to filter and notify the right people on occurring threats





