As the IoT industry continues to grow and evolve, so too does interest in protecting data integrity and confidentiality from IoT devices where data is collected, to the cloud where it is stored and processed. In fact, 72% of enterprises indicate that the device-to-cloud security is the key factor when choosing an IoT solution according to a GSMA intelligence survey from December 20201.
Despite the importance of IoT security for enterprises, there is a lack of universal standards for the authentication and authorization of IoT devices. IoT SAFE (IoT SIM Applet For Secure End-to-End Communication) enables IoT device manufacturers and IoT service providers to use the SIM (or even any other Secure Element) as a Root of Trust to secure IoT device-to-cloud communications by implementing the world’s most popular application layer security protocol2.
Increasing attacks on the IoT
Within the IoT ecosystem, devices collect, process and send data to the cloud, where various IoT applications are executed. But while the emergence of billions more IoT devices creates new opportunities for stakeholders, it also presents profound security challenges. Reflecting this, anti-virus and computer security service provider Kaspersky reported that IoT cyberattacks more than doubled year-on-year during the first half of 20215.
To address these threats, the IoT cloud service must have absolute trust in the data received from IoT devices. This is only possible by ensuring that both the device and the server are mutually authenticated.
However, the IoT is set to be characterized by fragmentation in terms of the OS (operating system) and chips employed. An array of open source and proprietary IoT OS variants is already on the market and, given the rich and varied mix of applications, hardware and connectivity encompassed by the IoT, it is likely that the market will continue to sustain multiple OS and chips for the foreseeable future.
As consequence it is clearly expected that proprietary IoT security solutions will not be able to scale or be duplicated. The critical challenge is, therefore, how the device middleware can leverage the security services embedded in Secure Elements (such as a SIM card) in a scalable manner.
IoT SAFE is a technology that makes it easier to deploy and operate an IoT solution that is secure, scalable, and manageable over time. It helps to solve the challenge of provisioning millions of IoT devices across an ecosystem by enabling provisioning and credential lifecycle management from a remote IoT security service2.
What is IoT SAFE?
According to the National Institute of Standards and Technology (NIST) Root of Trust is a highly reliable hardware, firmware, and software component that performs specific, critical security functions. Because Root of Trust is inherently trusted, it must be secure by design. Root of Trust provides a firm foundation from which to build security and trust4.
In the context of IoT SAFE which is providing a common procedure to secure IoT data integrity and confidentiality, a SIM card is functioning as the hardware Root of Trust (in an IoT device) as it has advanced security and cryptographic features and is a fully standardized secure element, enabling interoperability across different vendors and consistent use by IoT device makers3. It is also compatible with all SIM form factors, such as a standard SIM, eSIM, and iSIM. The following Figure 1 illustrates the IoT SAFE architecture based on SIM card as secure element.
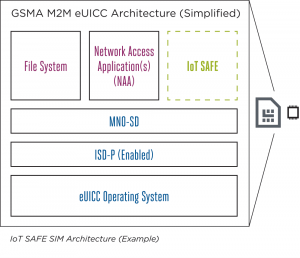
Figure 1: IoT SAFE SIM Architecture6
The IoT SAFE solution is built on four technical pillars. A software component is installed inside the device and used as a safe to store data encryption keys. This appropriate IoT SAFE applet (i.e. JavaCard applet) is linked directly to the SIM card and manages the new secure communication interface. Part of the software of the object itself must be modified to connect to this new interface using “device middleware.” The data to be sent is then securely transferred to a cloud. Finally, the object is protected by the IoT SAFE server. Since security is provided by the SIM, the carrier is the guarantor, meaning it can dynamically request keys, revoke them if security has been compromised, and even disconnect the object from the network7.
Summarizing the IoT SAFE provides security services (see Figure 2) that enable:
- IoT devices to securely perform mutual (D)TLS authentication to a server using either asymmetric or symmetric security schemes
- IoT devices to compute shared secrets and keep long-term keys secret
- Provisioning and credential lifecycle management from a remote IoT security service
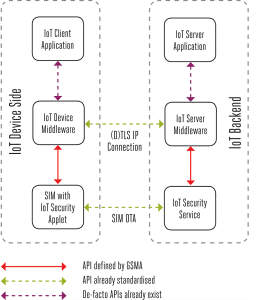
Figure 2: IoT SAFE System Architecture6
The main benefits are:
- Secure IoT data communications with cloud-based applications
- Helps solve the challenge of scalable provisioning for billions of IoT devices
- Maintains enterprise security features across different MNOs
- Robust, effective and scalable IoT security
- Agnostic from type of Secure Element
Conclusion
IoT SAFE is taking the world’s most popular end-to-end security protocol, Transport Layer Security and protecting the credentials used to put it in place, in the SAFEst place inside the device, the SIM, eSIM or secure element. This in turn enables the secure, seamless cloud-on boarding for enterprises leading to a full zero touch provision flow allowing cellular IoT connectivity to scale. IoT SAFE is connectivity agnostic meaning that it can work in the same way over the various categories of cellular network communications and any IP connected device featuring an (e)SIM (or even secure element)2.
References:
- GSMA intelligence: IoT security for enterprises: make it work, make it easy, December 2020
- IoT SAFE Whitepaper: Robust IoT security at scale https://www.gsma.com/iot/wp-content/uploads/2021/06/IoT-SAFE-Whitepaper-2021.pdf
- IoT SAFE: Executive Summary https://www.gsma.com/iot/wp-content/uploads/2020/05/IoT-SAFE-Executive-Summary.pdf
- Root of Trust https://csrc.nist.gov/glossary/term/roots_of_trust
- IoT Security Attacks https://www.iotworldtoday.com/2021/09/17/iot-cyberattacks-escalate-in-2021-according-to-kaspersky/
- IoT SAFE GSMA https://www.gsma.com/iot/iot-safe/#doc
- IoT SAFE: eSIMs as a digital safe https://hellofuture.orange.com/en/iot-safe-esims-as-a-digital-safe/





