In recent years the rapid proliferation of Internet-connected devices is driving an unprecedented growth of Internet of Things (IoT) systems and applications. This enables the evolving of the functionalities that they provide to end-users, but also in terms of the technologies that they comprise. Specifically, non-trivial state-of-the-art IoT systems comprise numerous devices, including not only conventional sensors and passive devices, but also smart objects and cyber-physical systems. Additionally, IoT systems are deployed in scalable edge/cloud computing infrastructures, which comprise broadband networks, edge gateways and devices, as well as cloud data centres. The rising sophistication of IoT systems provides the means for developing and deploying novel IoT applications, yet it also introduces significant cyber-security challenges. These challenges are evident in the scope of recent cyber-security incidents against IoT infrastructures and services which include:
- The emergence of new types of large-scale security attacks against IoT systems.
- Vulnerabilities in Cyber-Physical Systems (CPS), which are associated with the cyber resilience challenges of CPS systems.
- Security threats associated with the interplay between Information Technology (IT) and Operational Technology (OT) infrastructures.
- Complex Regulatory Compliance requirements in a demanding and volatile landscape.
To come up against these challenges there is a need for end-to-end solutions and tools that can protect IoT assets from the many different types of attacks. Security monitoring and security data analytics is one of the primary functionalities in this direction. Based on monitoring, analysis, and action workflows it is possible to monitor the various devices, systems and services that comprise an IoT system in effective and integrated ways. Accordingly, monitoring can then be a foundation for the identification, assessment, and mitigation of risks. Such a solution is the Runtime Monitoring System (RMS) that is going to be offered from IOTAC project. RMS will partially reuse and extend existent designs and implementations from a related system offered in the context of H2020 SecureIoT project [1].
IoTAC Runtime Monitoring System (RMS) will provide the specifications and relevant framework implementation to enable a real-time service which will collect security-related data from monitored IoT system components or application and store them for further processing. The collected data will be used to drive analytics algorithms that detect patterns of abnormal behaviour.
The system will feature lightweight monitoring probs that will be responsible for the data collection and publishing to the monitoring platform. The RMS will provide appropriate configuration and management mechanism over the monitoring probes as well as appropriate data models and data transformation engines that will enable the discoverability and reusability of the collected data. The probe management will be facilitated by an internal probe registry that will maintain the probe information along with their status and will enable the probe creation, reconfiguration, and discovery. The figure below illustrates a functional diagram of the main system components that is going to be offered.
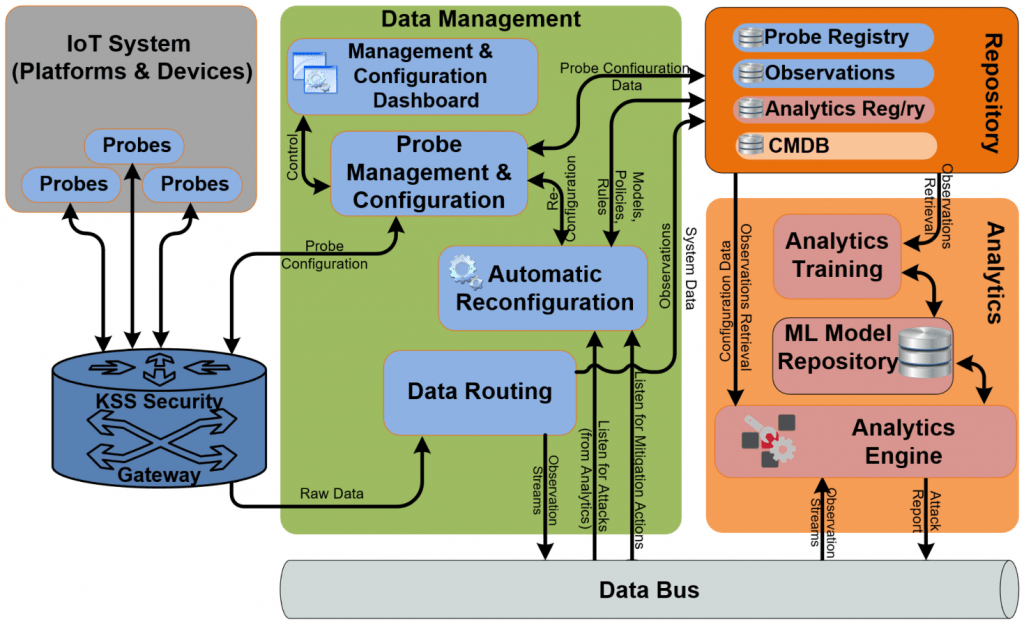
The different components along their interactions are:
- Data bus: which is a communications channel through which all real-time data are routed. Platform components may subscribe to the data bus to receive data of specific interest to them.
- Deployed probes: which collects data from the target IoT system or application and stream them to the IoT platform through the data routing component.
- Probe Management and Configuration: which is responsible for managing and configuring the deployed probes. The Probe Management and Configuration will enable the reception of automatic probe configuration commands and correspondingly configures the managed probes. Manual probe configuration commands may also be received by the dashboard. The Management and Configuration dashboard provides a user interface to the Probe Management and Configuration component.
- Probe Registry: which maintains a record of the deployed probes. Probe deployment data, as well as state and configuration data, are maintained by the registry. The registry provides probe creation, reconfiguration, and search capabilities. It facilitates the automatic deployment of probes and their dynamic discovery.
- Automatic Reconfiguration: which receives abnormal behaviour reports for the monitored system and sends automatic probe re-configuration commands based on a predefined scenario.
- Data Storage: which contains historic security data that have been collected by the deployed probes. These data can be used by the Data Analytics to train itself and produce a set of security templates that will be used subsequently for identifying security issues on the target IoT system.
- CMDB (part of the Data Storage): which contains information about all assets of the Runtime Monitoring System related to the monitored System along with their attributes and configuration parameters.
The system will run on the cloud as a service and is going to connect with the KSS gateway to confirm the validity and trustworthiness of the deployed probes that deliver monitored data to it. The RMS will enhance the KSS gateway abnormal behaviour detection by enabling user data monitoring other than the network data that the KSS gateway monitors.
[1] Aikaterini Roukounaki, Sofoklis Efremidis, John Soldatos, Jürgen Neises, Thomas Walloschke, Nikos Kefalakis: Scalable and Configurable End-to-End Collection and Analysis of IoT Security Data: Towards End-to-End Security in IoT Systems. GIoTS 2019: 1-6




