The CERTH/ITI Smart Home is Greece’s first house that combines advanced construction materials with intelligent ICT solutions, resulting in a future-proof, sustainable, and active testing environment. It offers a variety of innovative smart IoT-based technologies, including energy, health, big data, robotics, and artificial intelligence (AI). The Smart Home is equipped with a wide set of heterogeneous sensors and actuators providing information for several operations taking place within its infrastructure (e.g., smart light bulbs, smart appliances like smart washing machine and smart refrigerator, etc.).
Information Security is a major concern for any ICT system, and the ITI Smart Home is not an exception. Energy and Health modules apply and maintain diverse controls across the wide network of heterogeneous interconnected IoT sensors and actuators. Smart Home inhabitants have the possibility to switch on/off appliances using dedicated software services. Besides, sensitive information such as energy consumption or outputs of healthcare sensors is constantly exchanged between built-in services via the Smart Home network. This implies a large attack surface and a significant challenge for appropriate security controls across the whole system.
Considering the aforementioned risks, the security concerns pertaining to the Smart Home can be categorized into two main dimensions. Firstly, there is a need to address the potential risks associated with the execution of malicious commands and the reporting of falsified sensor or device measurements to the Smart Home administrator. To this end, a more secure policy is needed for identifying if the reported measurements are accurate or not, or more specifically, if they have been altered in a malicious way by an intruder. Secondly, we must ensure security measures are in place to prevent unauthorized access to the resources and data within the Smart Home system. Regarding authentication and user access control on the resources of the Smart Home system, a combination of basic authentication and role-based access control is currently used, which defines to which resources the user has access and what actions the user can perform on these resources. We consider that this scheme is adequate for some cases, but it has room for improvement.
To this end, within the H2020 IoTAC project, the Smart Home infrastructure serves as a successful test bed to evaluate the proposed IoTAC security solutions. By deploying the innovative IoTAC security solutions in the Smart Home System, we can effectively address both of the aforementioned security concerns. Figure 1 depicts a high-level overview of the integration of the novel IoTAC security modules into the Smart Home infrastructure.
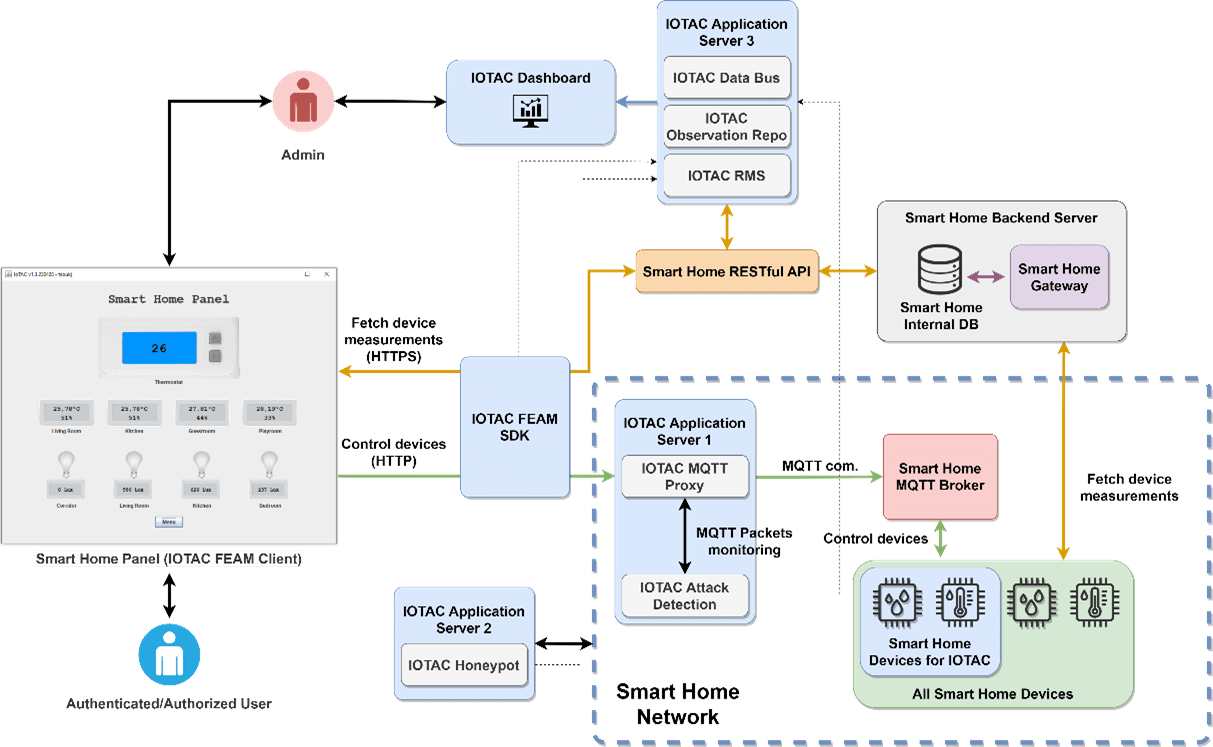
Figure 1 – High-level Overview of IoTAC Integration in Smart Home
To address the security concerns in more detail, the deployment of the novel runtime monitoring features of the IoTAC framework plays a crucial role. Specifically, the IoTAC Attack Detection (AD) and Honeypot modules effectively alleviate the concern of executing malicious commands and reporting altered device and sensor measurements to the Smart Home administrator, ensuring the integrity of the reported data. Supporting these modules is the IoTAC Runtime Monitoring System (RMS), which facilitates data distribution and provides security-related information to the Smart Home administrator, such as the number of identified malicious attacks and affected devices.
Additionally, to mitigate the security concern of unauthorized access to Smart Home resources, the IoTAC FEAM (Front-End Access Management) module is deployed. This module introduces novel authentication and authorization mechanisms that enhance the registration process for users in the Smart Home System and regulate their access to resources. By leveraging FEAM, the protected system is secured against unauthorized access attempts.
Finally, in terms of design time security, all newly developed applications and services undergo evaluation and certification by the Software Security by Design (SSD) platform. This ensures that these components meet rigorous security standards before integration into the Smart Home ecosystem.
As the integration of IoTAC into the Smart Home enters the validation phase, there is a high level of confidence that incorporating the novel IoTAC hardware and software security solutions will significantly enhance the overall security of the Smart Home environment. More details on the results will follow in the upcoming pilot-related public deliverables. Stay tuned!





