While the Zero Trust Model of Cybersecurity was created by John Kindervag back in 2009, it has become a buzzword in recent years, and more of a priority due to COVID-19 and the remote work economy, as it offers an optimal way to address current security challenges for a cloud-first, work from anywhere world.
What is Zero Trust?
The traditional approach to cybersecurity is determined by the concept of what is inside the corporate firewall can be trusted. Organizations protected themselves by putting a perimeter around their network, everyone inside the network was trusted, and everyone outside the network was not. The organizations were operating under the motto “Trust, but verify.” In the trust-but-verify model, trust is the default. When identity is verified, trust is assumed, and access is granted. But identity credentials can be stolen, networks can be hacked, and it is impossible to know with certainty if the originator of network traffic can truly be trusted. The perimeter-based security offers insufficient protection against the advanced persistent cyber threats targeting us today. Once an intruder is discovered in the system, it is already too late. If a hacker breached the network, they had access to everything inside the perimeters.
John Kindervag, back then working as a security analyst with Forrester, created the concept of Zero Ttrust, which is based on the principle that no network user, packet, interface, or device—whether internal or external to the network—should be trusted. Zero Trust eliminates the concept of trust from cybersecurity strategy, and every user, packet, network interface, and the device is granted the same default trust level: zero. Users inside a network are no more trustworthy than users outside a network. Zero Trust assumes that all traffic in an organization’s network is threat traffic and restricts access to any data only to those authorized.
The concept of Zero Trust is “Never trust, always verify”. Networks should be designed without implicit trust, enforcing strict identity verification and access policies based on the least-privilege principle for every user, device, or application, regardless of whether they are located within the former local area network or somewhere on the Internet.
The verification process is one of the key aspects of zero trust, assuming that the end-user, device, and network from which they are requesting access are hostile until proven otherwise. Every access request to a resource must be thoroughly evaluated dynamically and in real-time based on access policies in place and the current state of credentials, device, application, and service, as well as other observable behaviour and environmental attributes before access may be granted. A user may be verified and granted access to a specific resource, but all other resources are kept invisible (“blacked out” or “dark”) to them, and will still need to be reverified to access another resource. The continuous review prevents the lateral movement of bad actors from spreading from compromised systems within network environments.
Identity is the new perimeter
With widespread mobile access and cloud computing, organization perimeters have dissolved, and organizations can no longer assume that users in a network should be trusted. A perimeter is needed around every user, which accesses data in the organization. In today’s digital landscape, identity is the new perimeter.
Identity and Access Management (IAM) policies and technologies become central in controlling users, devices, data, and their networks, as they provide visibility and control over which users have access to what resources and minimize risks such as compromised credentials or incorrect provisioning or authentication.
By evolving the network-centric focus and considering areas such as Identity and Access Management and Privileged Access Management (PAM) amongst others, the term Zero Trust eXtended (ZTX) Ecosystem was born in 2017, by Forrester analyst Dr Chase Cunningham.
Actually, identity-first security is listed as one of the eight security and risk trends this year, in Gartner’s recent “Top Security and Risk Trends for 2021”1.
NIST “Zero Trust Architecture”
In 2015 a data breach at the U.S. government Office of Personnel Management (OPM) exposed 22.1 million records of personally identifiable information of people who had undergone background checks. This was one of the largest breaches of U.S. government data in history and sparked initiatives to improve and modernize the U.S. government’s security framework.
In August 2020, NIST, the US National Institute for Standards and Technology, published a special publication 800-207 “Zero Trust Architecture”, with the goal to secure U.S. government information systems and infrastructures. The document formulates the following definition: “Zero Trust (ZT) provides a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised. Zero trust architecture (ZTA) is an enterprise’s cybersecurity plan that utilizes zero trust concepts and encompasses component relationships, workflow planning, and access policies. Therefore, a zero trust enterprise is the network infrastructure (physical and virtual) and operational policies that are in place for an enterprise as a product of a zero trust architecture plan.”2
Zero Trust for IoT/OT device security
IoT/OT device security is one of the hardest problems to solve within the enterprise. The IoT device explosion has introduced a massive area of potential compromise for networks and enterprises.
This has led to the reconsideration of the concept of identity – every connected thing has an identity and must be under scrutiny within the Zero Trust Framework. But truly understanding every device requires much more than simply identifying their IP addresses, manufacturers, and model numbers – comprehending business context, traffic flows and risk potential is essential.
Implementing a Zero Trust model
The Zero Trust concept requires a major shift in many aspects of IT (and business processes) of an organization which cannot be completed overnight. Organizations work to implement a Zero Trust architecture built around identity-driven security practices, i.e. integrate the security architecture with an IAM solution.
For the Whitepaper “The State of Zero Trust Security 2021”3 OKTA conducted a survey of 600 security decision-makers at global companies across multiple industries and asked what other tools they have integrated or plan to integrate with their IAM system. The survey found that the most common integrations in place today were endpoint protection (EMM) and cloud access security brokers (CASB) — at 77% and 69% of companies (see Figure 1). Most companies selected security information and event management (SIEM) as the most important tools to be integrated with IAM for supporting Zero Trust protection (see Figure 2).
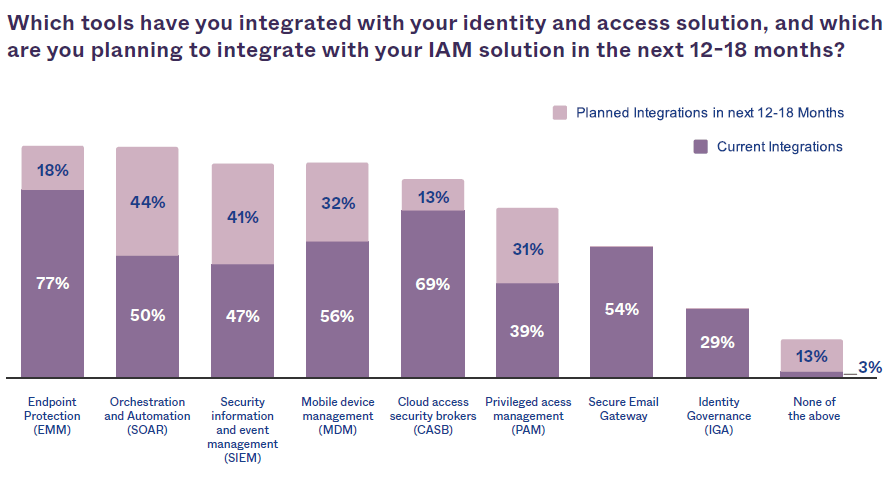
Figure 1 – OKTA Survey3: Tool Integration
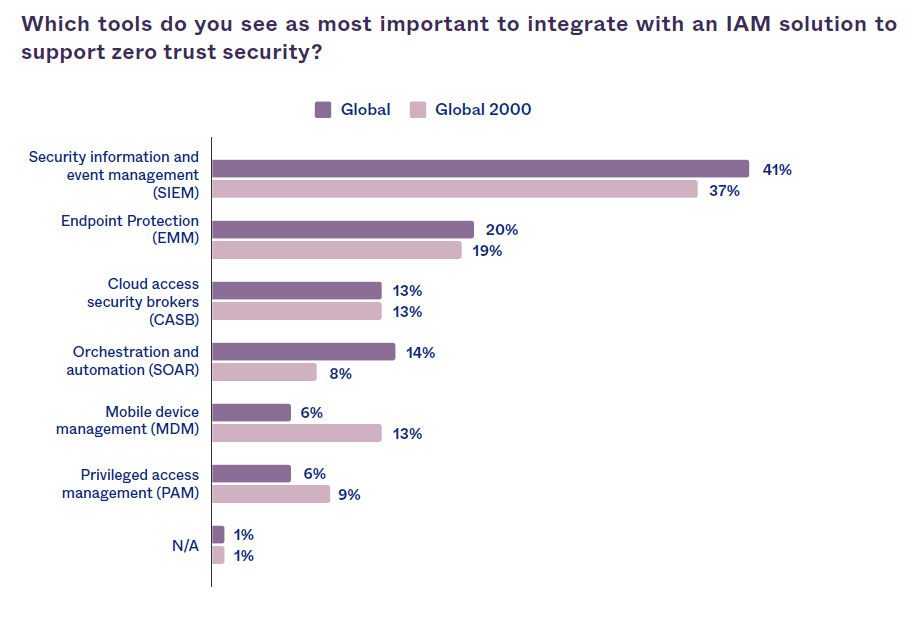
Figure 2 – OKTA Survey3: Most Important Tools to Integrate
Cyber-attacks today are identity-based and credential-based intrusions, against which perimeter-based security no longer provides protection. The solution is Zero Trust, with the “never trust, always verify” approach, and assigning just enough privilege at just the right time. This concept supports mobile and remote workers as well as the ever-growing number of IoT devices.
IoTAC with its Front-End Access Control system provides a tool that supports the Zero Trust paradigm which is further enhanced by the complementary runtime security modules, the secure IoT gateway, the AI-based attack detection module, the honeypot and the runtime monitoring system of the overall architecture.
References:
- Gartner Top Security and Risk Trends for 2021 https://www.gartner.com/smarterwithgartner/gartner-top-security-and-risk-trends-for-2021/
- Zero Trust Architecture https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf
- The State of Zero Trust Security 2021 https://www.okta.com/sites/default/files/2021-07/WPR-2021-ZeroTrust-070821.pdf





