The new IoTAC security model for IoT architectures will be deployed and validated in four different pilots, representing diverse industry domains.
In the case of the Airborne (drone), the pilot will focus on the vulnerability of Unmanned Air Systems (UAVs) and the vulnerability of fixed sensors that are in remote locations without human protection. Such systems are used for civil protection against large disasters (e.g. firestorms), while they can also be extended to monitoring critical infrastructures such as roads or railways.
A model of the system will be established with user workstations, a ground control station (GCS) for UAVs, access points, and nodes. The system will be built around a hybrid communication network that combines fixed lines and wireless segments. The mobile sensors, UAVs, satellites will also be complex systems with their own protection systems.
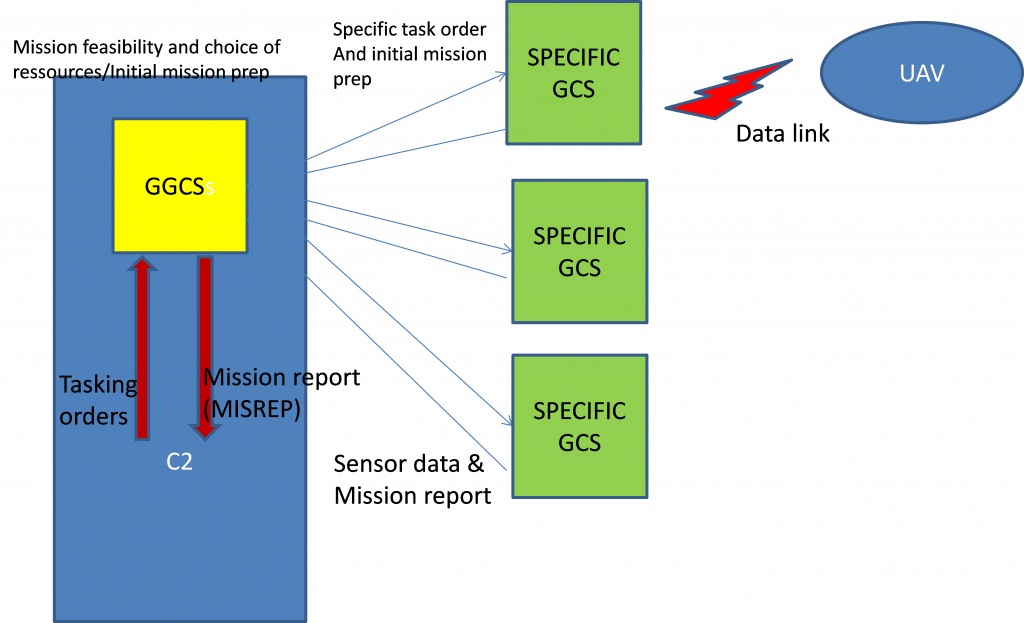
Figure 1 – Architectural overview of the Drone pilot system
The demonstration aims to test the solutions developed in the project to protect large distributed systems against attacks. The challenge is to detect intrusions in the system and the resulting attacks. The pilot will consist of testing the runtime monitoring features implemented by the project and solutions to counter the possible attacks on the system.
The Drone Pilot System is used by operators to monitor a predefined area. There are sectional centres in charge of different portions of the area, equipped with a Command and Control (C2) system. The centres employ field patrols on vehicles and/or walking. Several types of UAVs are used to help the patrols to detect any noteworthy phenomenon (fire, flood, etc.). Some of the UAVs are medium/long-range (fixed wings) and are managed directly by the sectorial centre and others are short-range (VTOLs) and are managed by the patrol commanders in the field. Some Specific Ground Control Stations (GCSs) are therefore deployed in the field and are sometimes left unattended.
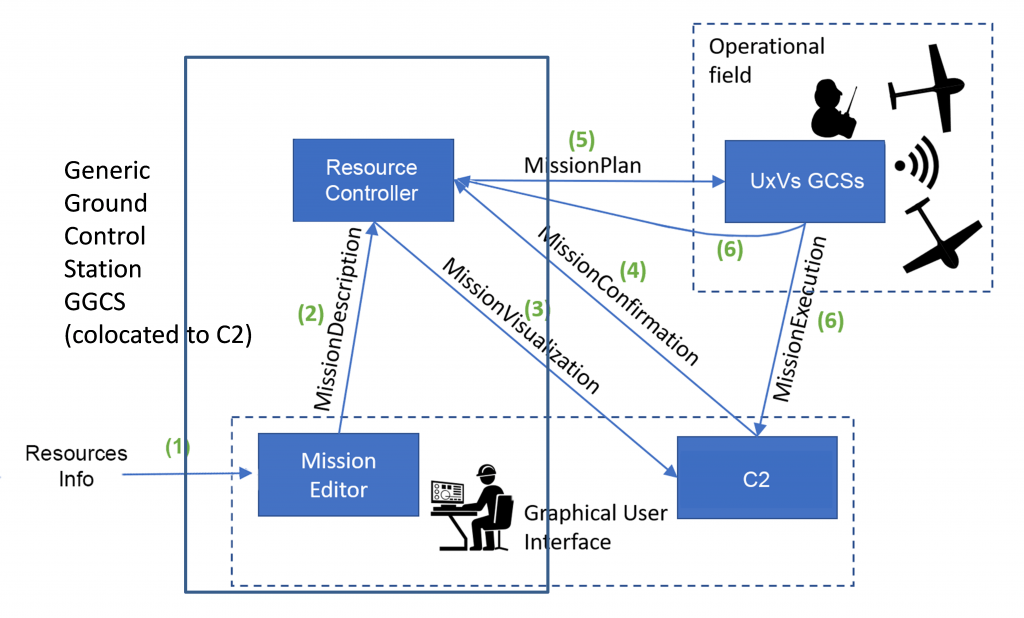
Figure 2 – Communication overview of the Drone pilot system. Green numbers denote a typical message sequence.
Human participants in the demonstration architecture are:
- C2 operators at the sectorial centre, operating the C2 and the GGS
- Field Commanders (patrols) that operate small UAVs directly through the GCSs.
- Pilots of the UAVs.
Major behavioural scenarios
- Operators are monitoring the UAVs missions through the respective data links (upstream and downstream). The data links are based on WiFi technology and respect the STANAG 4586.
- Most of the UAV missions are automatic. The data link is used for safety or mission re-tasking. If the link is lost, there are safety devices: the UAV takes an hippodrome pattern and wait for the data link to be re-established or (when it’s too long most of the time) automatic return to base.
- The pilots operate the GCS and the mission controllers monitor the mission and re-task where necessary.
Major communication channels:
- Specific data link grouping uplink and downlink, based on WIFI technology. The uplink sends piloting data and sensor management orders. The downlink sends to the GCS the sensors data (video flows, pictures for the EO/IR cameras).
- there is a protocol (message formats) defined between GGS and GCSs. The communication is general wireless and depends on the radio coverage. Satcom can be used.
- The data link is very directive and there is no broadcast, so the interception from a third party is unlikely. But it has to be improved.
The major threats faced by the system are:
- External people taking control of the GCSs and misusing the UAVs or destroying them.
- External people taking the control of UAVs through their data links (jamming the existing data link and/or using a more powerful emitter).
- Cyberattack against the sectorial centre.
The goal of the pilot is therefore to demonstrate how IoTAC solutions can mitigate and/or respond to these kinds of threats.





